
Do you worry about what hackers are up to now? You should be. Businesses and nonprofits are big targets because they often believe they don’t have the resources to invest in cybersecurity services. Time to change that thinking with affordable network security and unified cybersecurity platform from PC Professional in Oakland, CA.

You’ve worked too hard to establish and grow your Bay Area business for it to be compromised by data theft. And let’s be honest—one bad headline in the news can be all it takes to severely damage your business’s reputation.
PC Professional is one of the most trusted network security service providers in the San Francisco Bay Area. We are dedicated to protecting your users, devices, & workplace perimeters against cybersecurity breaches.
Get the most comprehensive, up-to-date protection against phishing, malware, ransomware, and other cyber attacks from PC Professional—so you can worry less and ensure that your products and sensitive client data are safe.

1
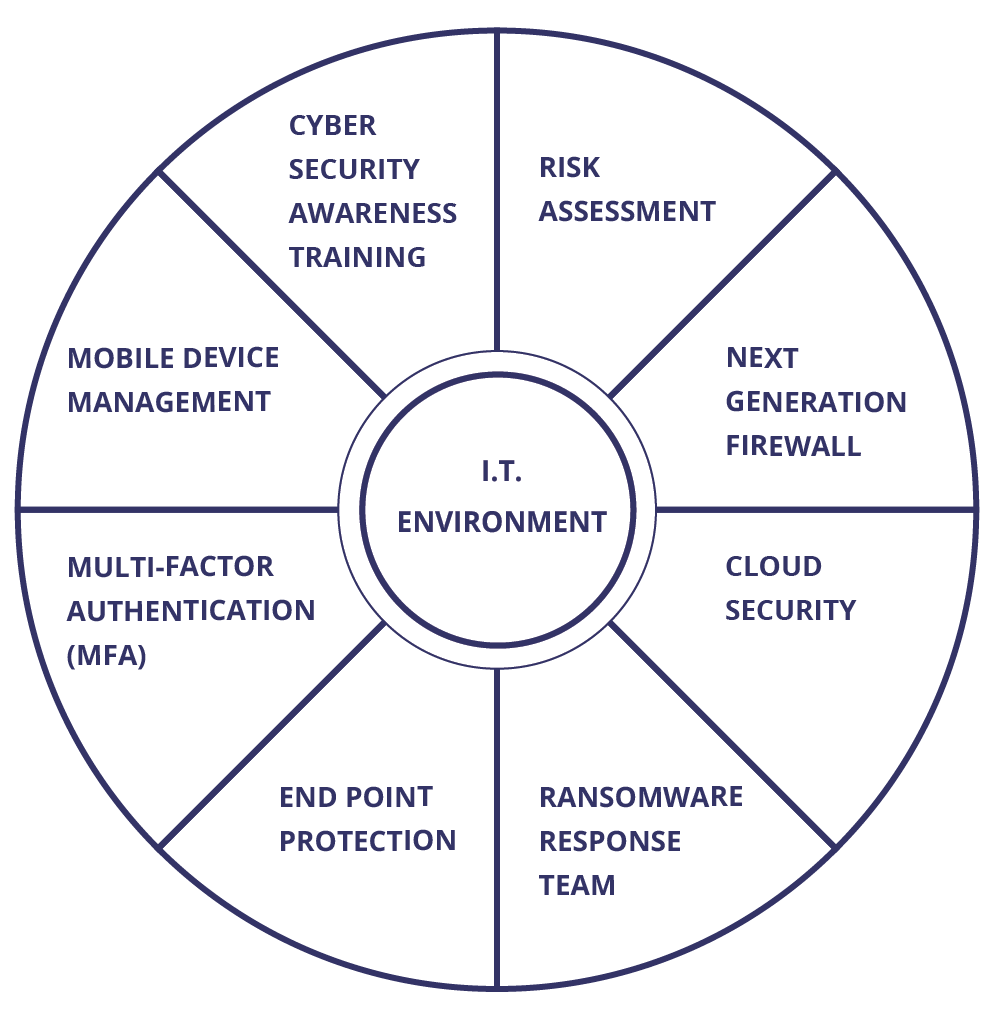
Our team of IT experts will analyze your environment, look for potential security gaps and make recommendations to help secure your organization from online threats and cyber attacks.
2
We offer the latest in Next Generation Firewall technology with intelligent security to the application level, Intrusion detection and prevention, secure VPN, SD WAN, and more.
3
We partner with Microsoft and other leading cloud service providers to deliver a high level of cloud security with compliance in cloud and hybrid environments.
4
In the event of a cyber attack like ransomware, our expert team will help identify and block the threat, while taking steps to help your organization restore critical IT services and data.
5
We partner with leading security applications to deliver managed protection for your devices against malware, phishing, and other cybercrimes.
6
Get multi-factor authentication services to add another layer of protection to help defend your data and prevent account compromises.
7
You can securely manage company-owned and BYOD mobile devices’ access to network resources and more with mobile device management.
8
Educate your employees on common IT security threats and types of cybercrime to reduce the risk of cybersecurity breaches that endanger your business.
9
What’s keeping your business from getting the best cyber security insurance rates? Find out with our Cyber Security Readiness Program.
Employee Cyber Crime Education is Often Overlooked
Educating your employees and stakeholders is vital in strengthening your protection against cyber threats. Everyone in your organization must be aware and on guard, knowing how to treat emails and file attachments—especially when they come from an unfamiliar email address.
Find out if your current data protection and backup strategy can effectively defend against cyber attacks and breaches.
A cyber attack is an unauthorized attempt to access a computer device, computer system, or an IT network. The goal of a cyber attack is to disrupt, disable, alter, or take control of the system. In many cases, the data within these systems are stolen, held for ransom, or even deleted.
The most common types of cyber attacks include denial-of-service (DoS), an attack that uses up the resources of a system to the extent that it can no longer respond to genuine server requests.
There’s also phishing, which sends emails from seemingly legitimate and trusted sources with the intent to collect sensitive information from the recipient.
We can’t forget the alarming prevalence of ransomware that targets both large and small companies. A recent, highly publicized ransomware case involved a major pipeline, meat supplier, hospitals, and an IT software company that services over 800 to 1,500 businesses globally. According to NBC News, ransomware costs in 2020 amounted to approximately $1.4 billion in America alone.
How can you protect your business from DoS, phishing, ransomware, and other attempts to steal information? Schedule a consultation and we’ll discuss your options.
The best form of protection is prevention. Zero Trust assumes that nothing behind a corporate firewall is safe until verified, regardless of the source. Although these constraints may seem drastic, today’s workforce’s reliance on computer networks and the massive repercussions of data breaches warrant diligent security as the norm to protect people and their devices.
Three steps must be replicated in all situations in order for Zero Trust protocol to work to keep your data secure.
1
Always authenticate user identity, location, device health, service or workload, data classification, and anomalies.
2
Limit user access to only what’s required for their title or position. Just-Enough-Access (JEA) keeps the right data in the right hands.
3
Limit the ability for hacks to spread laterally by segmenting access by network, user, devices, and application, with verification that each session is encrypted.
How can Zero Trust work to secure your business’s data? Let’s find out with a consultation.

In the case of a cyber-attack, many pieces of critical infrastructure and data can be compromised. Here are the major ones, with the ways we’ll help you to protect them.
✓ Verify Identity for People, Services, Devices
✓ Require Multi-Factor Authentication
✓ Ensure Compliant Access for Job Title
✓ Device Health Check Monitoring
✓ Secure Legacy On-Prem & Cloud Access
✓ Reduce Threats of Remote Work Perimeter
✓ Set Up Appropriate In-App Permissions
✓ Monitor Abnormal Behavior
✓ Gate Access Based on Real-Time Analytics
✓ Protect Data Wherever it Travels
✓ Classify, Label, Encrypt, and Restrict Access
✓ Assess On-Prem & and Cloud Servers
✓ Detect Attacks and Act on Risky Behavior
✓ Set up Just-in-Time Access
✓ Prevent Lateral Attacks Across the Network
✓ End-to-end Encryption
✓ Network Segmentation to Control Traffic
If you’re searching for a network security provider to check your current IT set-up, PC Professional is offering (for a limited time) a complimentary Cyber Security Assessment for businesses and nonprofits in Oakland and the San Francisco Bay Area.
This assessment includes an unbiased cyber security risk score and authentication from a qualified third party on your current level of protection against ransomware and other cybercrime attacks, and whether you might need a unified cybersecurity platform.
That’s right! You can find out if your network and data are vulnerable to cyber attacks for free. Why wait? Get your Cybersecurity Assessment today.
When you wish to learn more about information security, endpoint security, threat detection, and other network security and cybersecurity services, turn to the team at PC Professional. The more informed you and your employees are, the better protected you’ll be from cyber crimes.